Even though security remains one of the major concerns for an organization, the implication of new technologies has at the same time broadened and complicated the understanding of the term.
Security is no more about working in isolation.
Often events such as Drupalgeddon 2 have brought the question ‘Is Drupal Secure?’ to the center-table. Drupal is among those few open source projects popular for their security with a dedicated team working on to improve it. However, there are still sometimes when the security of your Drupal website is under the impression of threat.

Security is a vast area of expertise and it is quickly changing with time. No more is it about one person working in isolation or an expert who can understand all the aspects.
While the list of do’s and don'ts is extensive and exhaustive to keep up with the threats, vulnerabilities and mitigation strategies, here are the top seven Drupal security practices to follow in order to keep up the health of your website.
And Aristotle once said...
The aim of the wise is not to secure pleasure but, to avoid pain.
Best of Drupal 8 Security Practices
#1 Securing the Server-side Hosting Environment
Before starting off with the general security hacks and tips, you need to secure your server-side hosting environment. Here are some points to keep in mind before moving to securing your core.
- Protect the server: Only a limited number of users must be allowed to access your server. One of the key points is to add a basic layer by restricting the access to server login details. Once the authentication is set up, it is easier to monitor server access and restricting file access usage. This can help you detect unusual activities.
- Hide the server signature: Server Signature needs to be hidden as it reveals an important piece of information about the server and operating system. It can let a hacker know if you are using Apache or Linux - information which can be utilized as a vulnerability used to hack the server. In order to keep the server secure from possible vulnerabilities, you need to hide the server signature.
- Enable port wise security - Since the applications use the port numbers, it is important to keep certain port numbers hidden from general access.
#2 Securing the Drupal Core
- Keep your Core Updated
A key practice, keeping the core updated will always be the first when listing healthy security practices. And this was the first lesson we learned from the Drupalgeddon2. Always look out for core updates (include the minor releases as well) unless security is not on your agenda. In all of its advisories, the Drupal Security Team asks for updating the core version of the system.
If you fall a long ways behind the latest update, you are opening yourself to vulnerabilities. Since history tells us that hackers target the older versions.
Look out for core updates. Follow the Drupal security team @drupalsecurity on Twitter. Get quick updates and announcements from the team through the emails and security newsletter. You can also follow Security Group in order to contribute and stay part of the security discussions.
Another important point to note here is when updating the core - ALWAYS keep a backup of your site's database and codebase. We will discuss this security practice later in the article.
- Security by Design
As a matter of fact, every stakeholder wants security to be a simple concept, sadly it isn’t. One of the biggest misconceptions here would be that investing a hefty sum post development would ensure a secure system. However, it is never the case.
The best practice to follow is at the architectural level when the website is being designed.
Security by Design ensures that designing the software up by the ground to be secured in order to minimize the impact of a vulnerability when discovered. Pacing up your security from the foundation - is the key. It implies following the best security practices at the architectural level instead after building the website.
When the foundation of the design remains secure regardless of a reasonable approach adopted later, you can tackle the issues easily. A uniform methodology needs to be adopted to protect the assets from the threats.
Once the requirements have been collected, the architecture can be laid out and other elements can be discussed later like trusted execution environment, secure boot, secure software update among others.
"The key to security is eternal vigilance"
- Use Additional Security Module
When covering security, there is nothing as better than equipping yourself with more and more. To keep the walls up high, you can use the additional security modules like security kit, captcha, and paranoia. Drupal Security Review can be used as a checklist to test and check for many of the easy-to-make mistakes making your site vulnerable.
You can also look out for a List of Must Have Security Modules to prevent you from becoming the next victim of a potential cyber attack.
- Security kit
SecKit provides Drupal with various security-hardening options. This lets you mitigate the risks of exploitation of different web application vulnerabilities such as cross-site scripting (XSS), Cross-site request forgery, SSL, Clickjacking and other.
-
Captcha
A CAPTCHA is a reaction test put in the web structures to eliminate entry by robots. It helps in protecting your website’s contact and sign up forms asking you to prove your credibility as a human with a bizarre sequence of characters, symbols, numbers and sometimes images.Often they thwart you from accessing the content. Quite the irony, their purpose is contrary to what we reckon about them.
-
Paranoia
Paranoia helps you identify all the vulnerable issues/ places from where a potential leak is possible. It alerts the admin when an attacker tries to evaluate the PHP script via the website interface.
It helps in blocking the permission for the user to grant PHP visibility and creation of input formats that use PHP filter.
It also prevents the website to grant risky permission, mostly the ones that involve leaking the script information.
- Security kit
- But Use only Security Team Approved Modules
Your site probably uses a number of contributed modules, although that’s not an issue. Using the stable and approved modules is where the key lies. This is especially worth noting for contrib modules which are more susceptible to vulnerability.
Always look out for the green batch when downloading a contrib module. Rest, as the advisory reads, Use it at your own risk!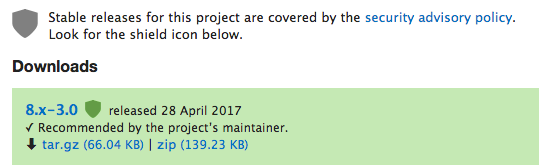
An example of security team approved module with a green batch 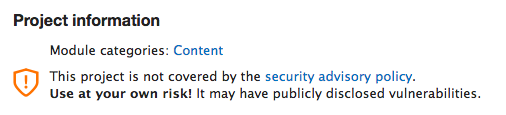
An example of a vulnerable module
#3 Backing Up - In Case of a Mishaps
- Keep Up your Backup
Catastrophes never come invited. While all seems perfect, you might wake up to find out that your website has been taken down by some psychotic hacker. Although it is an unforeseen event, you can definitely arm up yourself.
As an administrator, you have to be prepared for all of such uninvited events. They can be controlled and the damage minimized by strengthening security, frequent backups, installing updates in a timely manner.
We cannot stop disasters but we can arm ourselves with better security and backups. Hosting by Acquia cloud or Pantheon provide automated daily backups of your site’s database, files, and code plus single-click restoration if something goes wrong.
You can also use the Backup and Migrate Module or Demo Module because unlike life your Drupal website has the option to go back for some changes.
#4 User-Side Security
- Follow a Standard Practice with a Strong Password Policy
Passwords are used at both admin and user level, therefore strong and secure passwords are important for your website. When I say strong password should be used I have nothing against short and easy passwords. Easy should never imply less efficient.
A string like Mypassword123 will prove acceptable but is obviously weak and can easily be brute-forced.
The best practice? Your password should provide realistic strength in terms of measurement and complexity. A password must only be allowed as long as it proves to be of high enough entropy with a combination of characters, alphabets - uppercase and lowercase, symbols, and numbers.
Start checking passwords on explicit rules and amount of varying character types to be used (symbols, numbers, uppercase letters, etc).
Password Strength - a Drupal module - classifies the expected brute-force time for the summed entropy of common underlying patterns in the password. Patterns that can be detected in passwords include words that are found in a dictionary of common words, common first and last names or common passwords.
Your password can make the difference between a vulnerable and a hard-to-hack Drupal site.
#5 Set up a Firewall
The most common one is setting a firewall. Setting up a firewall provides additional protection over the web server and ensures the acceptance of connections only from trusted or known parties. Inversely, it restricts the outgoing of connections too.
#6 Check Files Permissions
Installing correct file permissions can allow a limited access to read, write or modify them. Permissions make a huge difference in security as they decide how compromising the platform can be for the hackers.
Similarly, the access to the important files like authorize.php, install.php can be blocked within the core files of the website and only permissible to the author and the developer.
#7 Enable HTTP Secure (HTTPS)
An SSL certificate can add on a layer of protection for your connection between the user and the server. This approach, restricts the hackers from crawling into your servers that might contain business critical information. An additional feature of the SSL certificate is that it makes you rank higher in the search engine’s optimisation process.
Further, Drupal websites are protected with the HTTP security headers that provide an additional layer of security. The header guide the browser about the site content and it’s treatment.
#8 Use Content Distribution Networks (CDNs)
Sensitive customer information like credit cards, passwords and application data always prone to attacks. Such data are often compromised under open gateways of APIs. They require the resilience and intelligence of a scalable network.
Similarly, the Denial of Service (DoS) attacks have continued to grow in volumes due to traffic and distribution of APIs.
CDNs such as Cloudflare, can be the intelligent solution for such threats and breaches of data.
In Summary
While there will always be some new thing to add to the list, you can be sure that this list comprises of the core practices which need to follow. The protocol for communication needs to be clear and well documented. Properly documented procedures are important, as third-party services can often be manipulated.
In need of a security update or services? Drop a mail at [email protected] and let us help you out.
Site builders and developers need to keep an eye open for the possible when security releases are announced and apply them quickly, to ensure the site is not compromised. It is good to be consistent and have your reasoning documented so that it is clearly understood.
Subscribe
Related Blogs
Inside the Drupal AI Summit: Themes, Speaker and What To Expect

“ The web is changing fast, and AI is rewriting the rules. It writes content, builds pages, and answers questions directly,…
FOST and Drupal AI Initiative: Next Era of Responsible AI

Three years after the launch of generative AI tools marked a new age for artificial intelligence, almost 90% of survey…
Drupal AI Ecosystem Part 5: AI Content Suggestions

Drupal has steadily evolved from being just a content management system into a flexible platform that incorporates emerging…




