Cyber security is an endless topic, somethings are crackable, and some just aren’t. The security discussions have become an endless thing and it is not going to stop. Sometimes facebook concerns everyone with its data related malpractices and sometimes Google but the crowd is here to absorb everything because even the government’s hands are tied to their knowledge and expertise base, they can hold them accountable but cannot ask them to shut business.
New threats emerge, defenses mechanisms and technologies keep improving but the attackers keep adopting new backdoors and new agencies to make sure they give us sleepless nights by threatening our data and making sure they are the attackers adopt new tactics, targeting hitherto unknown weakness.
Cyber isn’t that secure today
Thinking out loud here, what can be done to fit the gala of attacks, what new can be achieved to make sure these serial attacks don’t threaten people and the cyber peace so much?
So, what is being done to get back on attackers and prevent our critical systems? In the past organisations have build humongous digital walls and attackers have breached them repeatedly through some trick or the other. So what here should be done? What we have been doing is somehow isn’t enough these days.
The government needs to think differently, in a way which lays focus on how to continuously monitor and govern the nation’s IT security. A direction from the governing bodies of the nation would provide some key areas of security investment and areas which should be the private organisation’s prime focus. This would also bring more transparency in terms of which sectors are more vulnerable and investments and measures should be actioned likewise. It also would channel some budgeting decisions and making sure that investment decisions are forethought and will yield some security favourable results.
It's okay if it requires us to catch the lowest hanging fruits for a starter. Like for example, patching your systems frequently with the system updates will do the trick of keeping you away from the bad boys trying to breach your security wall round the clock.
Many whistleblowers have tried to uncover many security practises and bring down prestigious organisations to impact either economies or political agendas. There was always a reason to be attacked and be vulnerable. Organisations have always tried to do something or the other but guess what, we all know how complex things are sometimes and we need to collaboratively find a solution to things rather than just sitting on the sideline and waiting for things to correct themselves.
Some Cyber Security Statistics
The SSL store lists out some great cyber security statistics:
- The cybercrime economy is evolving at a rapid pace year by year as technology booms, it’s like a parallel and uncontrollable boom which has taken it to a whopping $1.5 trillion in profits every year. In total the cyber crime economy is considered to be worth a $1.5 trillion already.
- The value of the cyber security market is anticipated to reach $300 billion by 2024, according to a 2019 press release by Global Market Insights, Inc.
- There is a 9 percent increase in cyber security spending each year and it will only increase by 9% on average per organisation per year.
- Small or average businesses invest more than <$500 per year in trying to be secure on the cyber front, they spend money on cyber security products. Which eventually contributes to the income of the cyber security markets.
What is the right security spending for you?
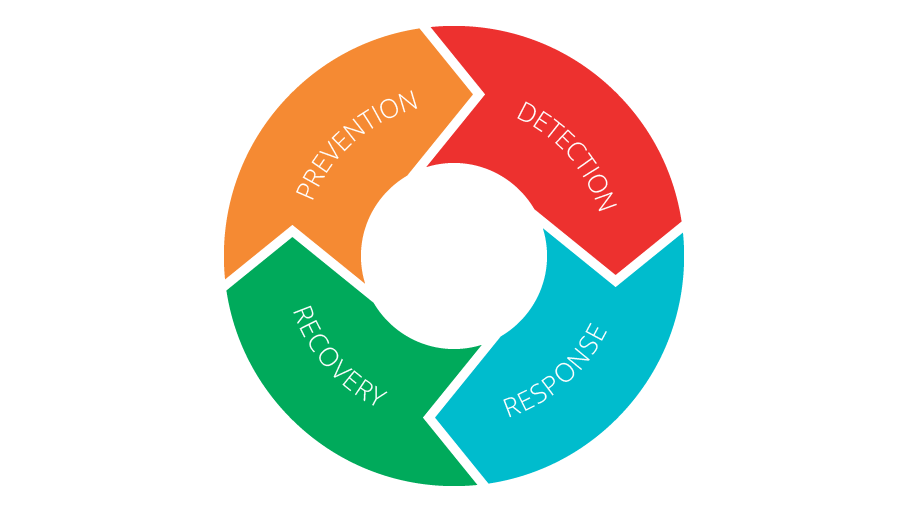
Security governance is an area which needs sheer expertise and strict protocols from both the management end executive end. This transparent governance ensures that there is a sense of continuous engagement and relationship between all the various processes like detection, prevention, response and recovery. Diversification in effort needs to be organisation’s prime focus. Effort needs to be applied in all the four independent but interlinked four areas and presented as a continuous loop.
- Are the right things being done?
- Are those things being done the right way?
- Are they getting completed in time?
- Are you reaping the right benefits out of it?
Coding practises get more secure, threat modelling is done more rigorously. This constant use of threat modeling, penetration testing during the purchase process of software assets is more of what is required in the current economic scenario.
What would be ideal is looking at every minute business function and making sure it is end to end secure throughout the organisation. Using this approach, you will be able to build a sustainable governance around your systems and ensure the right KPIs are held in place for smooth business functioning.
Final Word
Cyber security is becoming a rising concern and a set of good practises will get you rolling in this society surrounded by a group of people who like to make things vulnerable. Taking care of these points can be extremely rewarding in terms of your security related operations and can help you scale up a lean model for security.
Subscribe
Related Blogs
Trek n Tech Annual Retreat 2025: A 7-Day Workcation of OSL

OSL family came together for the Trek n Tech Annual Retreat 2025, a 7-day workcation set amidst the serene beauty of…
Exploring Drupal's Single Directory Components: A Game-Changer for Developers

Web development thrives on efficiency and organisation, and Drupal, our favourite CMS, is here to amp that up with its…
7 Quick Steps to Create API Documentation Using Postman
If you work with API , you are likely already familiar with Postman, the beloved REST Client trusted by countless…




