“A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being completely compromised.”
Warnings were issued in March 2018 for a highly critical vulnerability putting at risk at least a million websites. 28 March was decided as the day when the bug fix would be released to secure the websites.
The risk score which was earlier marked as 22/25 was now rated 24/25 (keeping in mind the proofs of automated attacks in the wild) and the bug dubbed as Drupalgeddon 2.
“Security risk: Highly critical 24∕25 AC:None/ A:None /CI:All /II:All /E:Exploit /TD:Default”
The vulnerability was identified as a remote code execution without user authentication and affecting the Drupal core of versions 6, 7, and 8. It allowed the attackers to take full control of any affected Drupal site which could apparently result in the site being fully compromised.
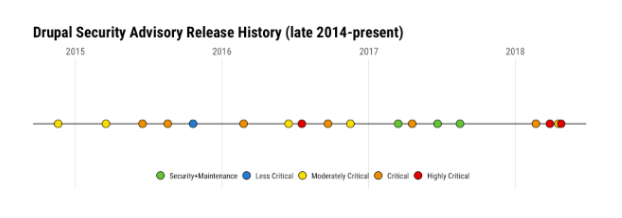
It is estimated (according to the Drupal project usage information) that over a million sites run on Drupal. And according to BuiltWith.com, the numbers are equivalent to about 9% of total websites. All at the risk of being compromised.
But this was not all, come April and there was another attempt to exploit the security of Drupal. What was it and how different was it from SA-CORE-2018-002?
“In April Acquia reported 26,000 attacks per hour across all its customers. How?”
Drupal Security Team rates the vulnerability according to its risk metrics and risk calculator.
Secure your website with Drupal modules. Here are Top 10 Drupal Security Modules for your website.
What are the Risk Parameters?
The present framework depends on the NIST Common Misuse Scoring System, where every weakness is scored and a number is allocated in the vicinity of 0 and 25. Drupal security updates marked above 20 is termed as critical.
The level is assigned by the Risk Calculator which takes different metrics into account. Following are some of the parameters on which the numbers are chosen.
Access complexity - AC - How easy or difficult is it for the attackers to exploit the vulnerability?
For SA-CORE-2018-002 | AC:None = None (easy for the attacker) +4 points
Authentication - A - What level is required to make an exploit successful?
For SA-CORE-2018-002 | A: None = None (all or anonymous users can attack) +4 points
Confidentiality impact - CI - If the exploit can make (non-public) data accessible?
For SA-CORE-2018-002 | CI: All = All non-public data is accessible +5 points
Integrity impact - II - Will the exploit compromise the system data?
For SA-CORE-2018-002 | II: All = All data can be modified or deleted in this exploit +5 points
Exploit (Zero-day impact) - E - Does a known exploit exist?
For SA-CORE-2018-002 | E: Exploit = Exploit exists (documented or deployed exploit code already in the wild) +4 points
Target distribution - TD - What percentage of users are affected?
For SA-CORE-2018-002 | TD: Default = Default or common module configurations are exploitable, but a config change can disable the exploit +2 points
Which calculates the total score as 24.
What can be done?
A successful exploit of the vulnerability can have a dramatic impact on the site. The only solution available is to upgrade Drupal core to the most recent version. However version 8.3x and 8.4x were not covered but the fix given for them, considering the severity of the risk score. And although the end of life has been announced for Drupal 6, there were solutions proposed for them too.
According to the Drupal Security Team, the advisory runs as:
- If you are running 7.x, then update Drupal core to 7.58.
(Apply Drupal security patch if, can’t upgrade)
- If you are running 8.5.x, then update Drupal core to 8.5.1.
(Apply Drupal security patch if, can’t upgrade)
All the versions above 8.1 are advised to upgrade to the latest version.
This issue also affects Drupal 6. Drupal 6 is End of Life. For more information on Drupal 6 support please contact a D6LTS vendor.
Story So Far…
The Drupal security team fixed the bug - SA-CORE-2018-002 - but that didn’t stop the hackers from attacking the unpatched Drupal sites. The exploit was not publicly known yet.
On April 12, 2018 Checkpoint Research provided a detailed explanation of the security along with a comprehensive guide on how to exploit the vulnerability. Another Russian researcher then shared a proof-of-concept exploit on Github.
This led to an increase in the number of attacks. In one of his posts, Dries writes ”...Following the release of the Checkpoint Research article, Acquia has tracked the origin of the 500,000 attempted attacks” which soared to 26,000 attacks per hour across all its customers.
On April 25, Drupal Security team released another advisory (SA-CORE-2018-004) which was also marked as Highly critical with the vulnerability marked the same as before - Remote Code Execution.
The advisory reads “This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being compromised. This vulnerability is related to Drupal core SA-CORE-2018-002.”
That severity rating was, however, one notch lower than "Drupalgeddon2".
The SA-CORE-2018-002 made it possible for attackers to remotely execute code of their choice on vulnerable servers, in that case simply by accessing a URL and injecting an exploit code.
After which numerous groups actively started exploiting the critical flaw to install cryptocurrency miners and malware that performs a denial-of-service assault on different servers.
It was also reported that among the many attacks that happened, efforts were made to install ransomware on servers that run the website for the Ukrainian Ministry of Energy. Acquia also reports that “over 50 percent of the attempted attacks Acquia has witnessed originate from the Ukraine”
Get in touch immediately to update your website, don’t hesitate to contact us at hello@opensenselabs. Our expert team and mitigation strategy will help you support immediately.
Subscribe
Related Blogs
Trek n Tech Annual Retreat 2025: A 7-Day Workcation of OSL

OSL family came together for the Trek n Tech Annual Retreat 2025, a 7-day workcation set amidst the serene beauty of…
Exploring Drupal's Single Directory Components: A Game-Changer for Developers

Web development thrives on efficiency and organisation, and Drupal, our favourite CMS, is here to amp that up with its…
7 Quick Steps to Create API Documentation Using Postman
If you work with API , you are likely already familiar with Postman, the beloved REST Client trusted by countless…




