Imagine you created something and that something is a software. You wanted your creation to be used by as many people as possible, you wanted to make it universally accessible. So, you did just that, you made the software source code accessible so that anyone could inspect it, modify it and enhance its capabilities.
This is the scenario that makes an open source software what it is; a publicly accessible tool that is all for the community. It honours open exchanges, collaborations, transparency and perpetual development that is community-centric. These principles have made open source software become immensely popular today. And here is proof of that.
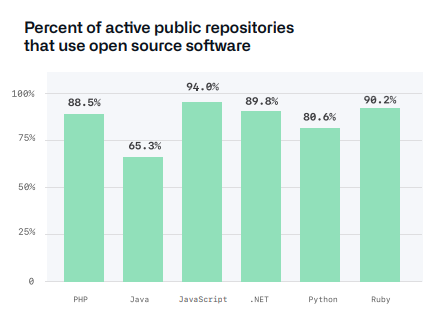
Many of the public repositories, like PHP, Java and .NET, use open source software and in heavy numbers. If we look at the revenue open source software is deriving, the numbers are again quite impressive.
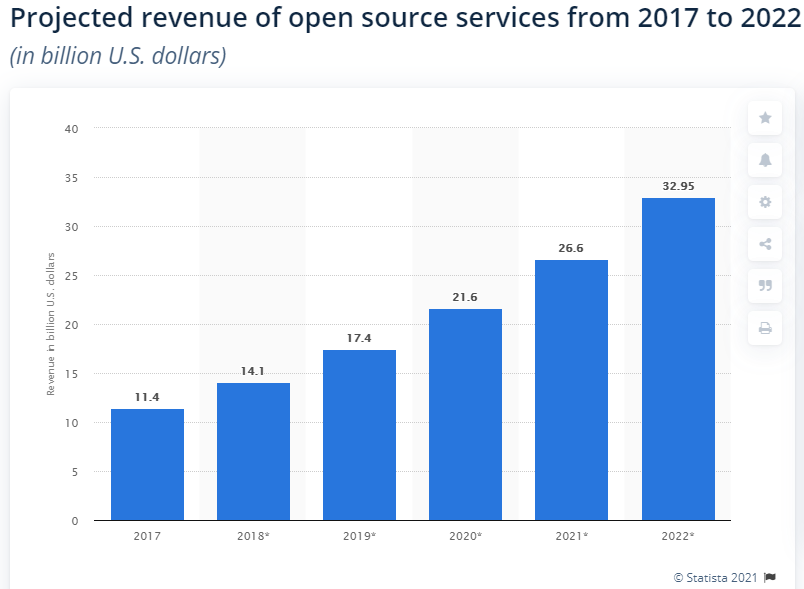
All these numbers speak volumes to the efficiency of open source software. However, if there is one aspect of open source software that needs some kind of assurance, I’d say it’s open source security. The reason is probably the fact that OSS is completely open for everyone, so it is assumed that something with this level of openness cannot be secure.
In this blog, we’ll try to find an answer to the question, ‘what is open source security’ and see whether it is actually secure or not.
What Is Open Source Security?
Today, businesses try to leverage multiple software in their efforts to move forward in technology and open source is one software that is omnipresent in these efforts, be it just for its code.
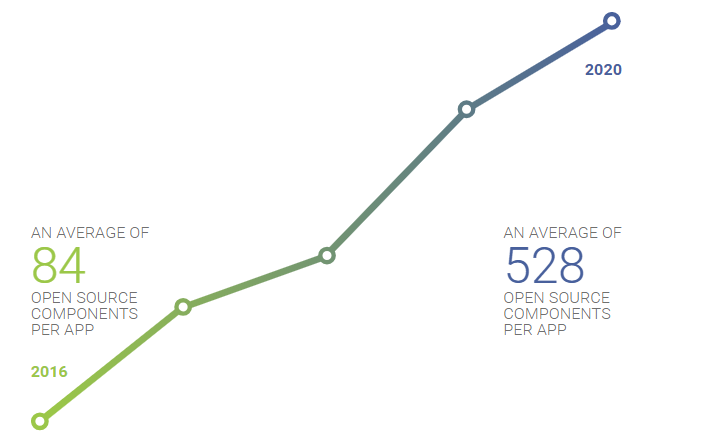
The reasons for this elevated usage of open source components are plenty.
The fact that you get to try the software before you buy it;
The fact that support is free;
The fact that there would be fewer bugs to deal with and faster fixes;
The fact that software security would improve;
To know more about the power of open source, read about the perks of being an open source contributor, leadership in open source, why are large enterprises investing in open source, why is open source recession-free, impact of open source during Covid-19 pandemic, and the significance of diversity, equity and inclusion in open source.
All of these account for open source to become a software that is quite pleasing to the eye. The last point that I mentioned may be the most pleasing factor of them all. But why? What is open source security? Is open source insecure? Let’s understand just that.
Like any other software out there, the OSS also goes through two main stages, the development and the production. And open source security works in both of them, managing and securing the OSS at all times by using certain tools and processes; all of this usually done through automation.
Talking about the Software Development Lifecycle, open source security has three main responsibilities;
- It identifies open source dependencies in your applications;
- It provides critical versioning and usage information;
- And it detects and warns about any policy violations and its consequent risks.
Moving on to the production phase, open source security continues to work diligently. Its main duties at this point are to focus on any and all open source vulnerabilities. It does so by;
- Monitoring vulnerability attacks;
- Blocking vulnerability attacks, if possible;
- And most importantly, alerting you for the same, thus making you ready to take action against them.
Be it a community driven open source or a commercial one, open source security works in much the same way.
Delving a little deeper in open source security, is there an initiative or a body that is accountable for it. This was one question that I found myself asking while researching about this piece. And there is, it is The Open Source Security Foundation. It helps organisations relying on open source software to understand their responsibilities in terms of user and organisational security and verify it.
The initiative focuses on aspects like vulnerability disclosure, security tooling and best practices, identification of threats and even digital identity attestation. All of these only aid in securing your projects, critical and otherwise, in a much better and efficient manner.
Is Open Source Good for Security?
The answer to the question ‘How does open source security work?’ is not a linear one. But if I had to answer it, I’d say open source security is nothing at all like Microsoft, which should provide a lot of clarity to you and instill a sense of faith in OSS.
According to Snyk’s The State of Open Source Security 2020 report,
Open source ecosystems have expanded by a third in 2019;
Open source security culture is focusing on shared responsibility;
Open source vulnerabilities have reduced by a fifth.
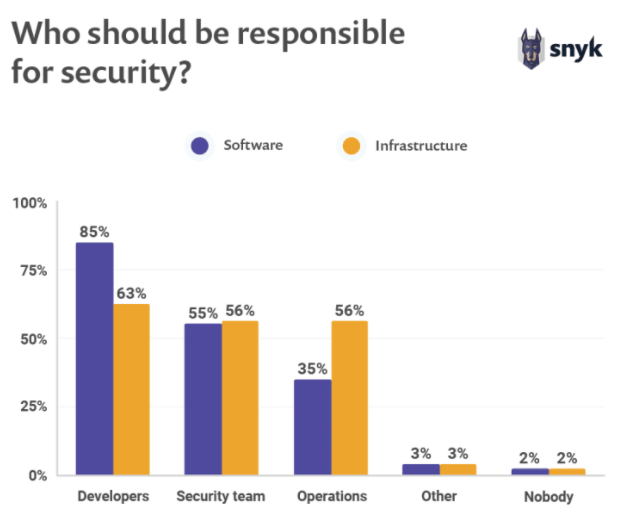
On top of this, the vulnerabilities that were found in open source as most reported weren’t high impact on software projects.
These facts were enough for me to believe in the capability of open source security. However, for you, I am going to provide four more reasons.
Security that is transparent
The main benefit of open source security is that it is transparent. What I mean by transparent is that its source code is open. You can get information about the code base and potential bugs.
People can sift through the source code of any open source project and improve any imperfections, which would not have been possible if the source code wasn’t open. This further means that there won’t be any surprises as the chances of any malicious functionality would be quite slim with this level of scrutiny.
Security that is reliable
This advantage is relatable to the previous one. OSS openness has made it possible for its code to be continually tested.
The online community, which is responsible for developing the code, is behind these tests, making the software more reliable and trusted. The software developed on such trust would most likely never crash and fail.
Security that provides quick catches and fixes
After transparency and reliance comes the benefit of quick fixes. The open source community is again to be thanked for this. The many contributors of open source make it possible to detect any bugs and flaws and quickly patch and fix them, without any elongated downtime for your applications.
Security that is sustainable
Open source software isn’t going to go anywhere and would open source security become antiquated. The reason would be its growing community that would continue to expand indefinitely. Therefore, the platform would continue to improve and you would have the assurance of better security means as time continues to move ahead.
At the heart of every benefit of open source security is its openness and community. Is open source a security risk? Not really. Is it a full-proof solution? Again not really. Yes, open source security cannot provide you the guarantee of being full-proof at all times, but the fact that the open source security at least provides a better chance of being secure is enough to make it advantageous for us; after all, are there really any guarantees in life?
Are There Challenges That You Need To Overcome?
Moving on from the pretty picture of open source security, let’s focus on the dark side of the concept. Open source security isn’t always full of the joys of spring, there are certainly challenges that need to be overcome. Since open source has become prevalent in every business sector, so have the open source security vulnerabilities.
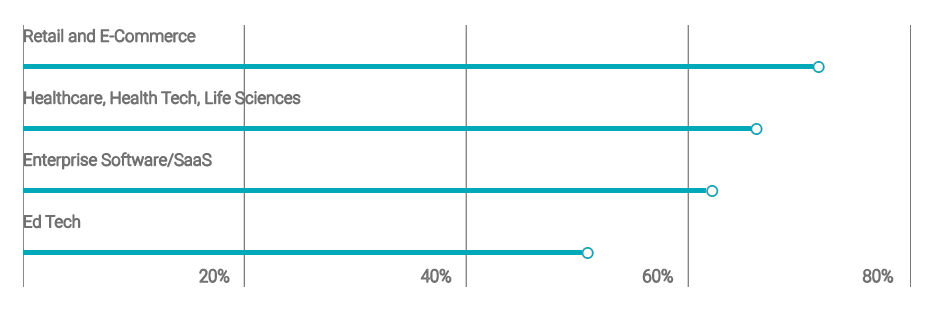
Ironically, most of the challenges coincide with the openness of an OSS, so the benefits become the drawbacks. Let’s take a look at them.
The openness isn’t without vulnerabilities
Much like any software out there, open source also comes with some vulnerabilities. Yes, the open source community aids in the remediation of these flaws, but they tend to widen the difference between open source safety and open source attacks.
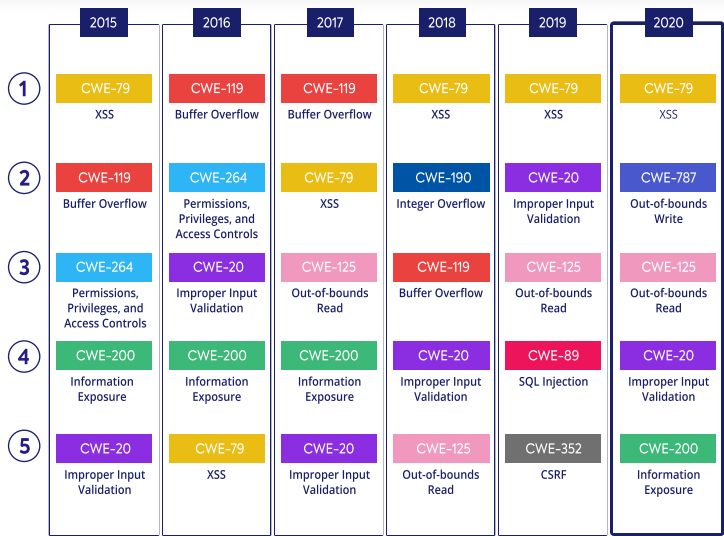
Yes, open source security issues come with their fair share of vulnerabilities, from XSS to information exposure, there is everything and these vulnerabilities keep on changing year after year.
However, there is a silver lining in this challenge and that is the impact of these vulnerabilities.
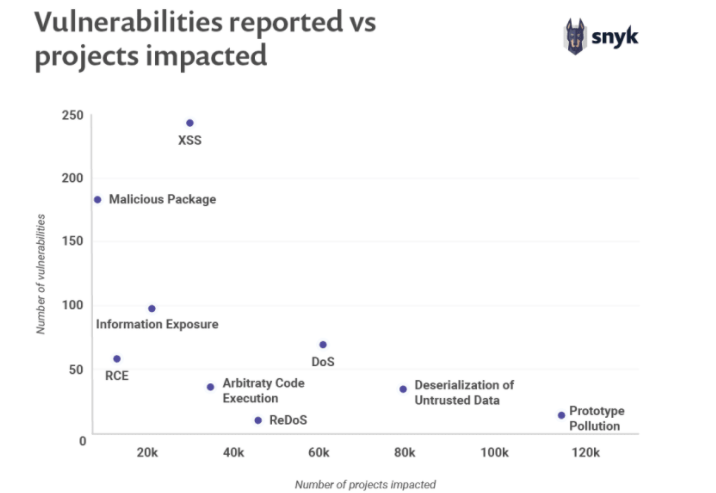
XSS is one of the most reported vulnerabilities, however, it only impacts a low number of projects. This can be considered as a positive outcome of this particular challenge.
The openness lures attackers
The OSS code is open for everyone and so its vulnerabilities; and we certainly know that everyone includes people with malicious intent as well. So, open source vulnerabilities become an easy target for attackers.
The National Vulnerability Database, which is a platform providing information about the open source vulnerabilities that too publicly isn’t helping this challenge much. Don’t get me wrong, such platforms are indeed helpful in identifying the problems, but considering they are public and open, the attackers get their arsenal for the next target.
You may think that the known vulnerabilities should get fixed before the attackers are lured in by them. But that is easier said than done. The problem here is that the open source vulnerabilities are published at multiple platforms, thus tracking them becomes difficult. Even if they have been located, updating, patching or fixing can require some time and during that phase, you’d be at risk.
The openness might overlook quality
There are a number of people who contribute to open source security and you cannot be sure that all of them would be security experts. Everyone in the community will not have the same level of skills and expertise. Therefore, the way they would create a piece of code would be different. This makes quality assurance a task that could almost be impossible to take on. Furthermore, the fact that there are no set standards for the quality of open source code makes it all more convenient to overlook quality..
All of this means that the quality might be overlooked and even compromised. The fact that only 8% of the WhiteSource survey respondents were concerned about the quality is a testament to this challenge.
The openness comes with licensing risks
OSS may be free to use, but it does come with a number of licenses that need compliance; 110 licenses to be exact, according to the Open Source Initiative. These act as the guidelines for OSS source to be used.
With these many licenses, there is bound to be a risk of compatibility. Let’s understand this, some licenses are compatible, this means you can use them together. However, some aren’t, which means that using them together would put you at risk, like the Apache 2.0 and GPL v2 license.
What’s more is that, if you do not comply with the licensing guidelines of open source, you’d be making yourself open to a lawsuit. While I know this isn’t the kind of security concern we've been talking about so far, it is a security concern all the same.
Can You Overcome the Security Challenges?
The major challenge in open source security are the vulnerabilities. Detecting them and resolving them has to be the priority, if you want to overcome the challenges. Given the fact that open source vulnerabilities have risen in 2020, you need to be sure that you are not at an elevated level of risk.
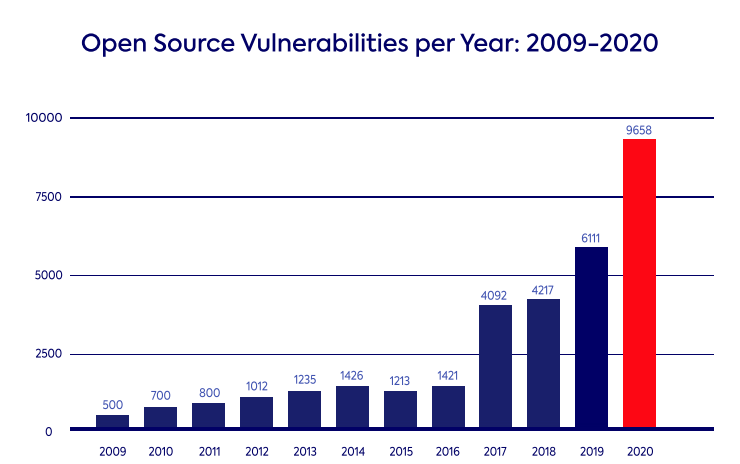
Let’s see how these vulnerabilities can be caught in time, so that they do not affect your business by implementing some of these open source best practices.
Prioritising security, always
The first part in overcoming open source vulnerabilities is to always prioritise security. This starts with the choice, whenever you choose an open source component to work with, security has to be one of the considerations in the choice.
Usually, functionality comes as the main reason for choosing an OSS. However, just focusing on that can put you at a disadvantage. Think of it this way, an open source component that does not require any integrations with your codebase would remove any and all security risks, along with reducing the complexity of your source code.
Prioritising automation as a means to detect and monitor vulnerabilities
Next comes the detection of the security vulnerabilities and automation comes quite handy here. Organisations, especially large ones, have a pretty massive codebase and going through it would be a mammoth task, if not automated. Detecting susceptibilities is already quite a lengthy process, even with automation.
You have to identify which packages are being used;
You have to pinpoint the vulnerable functionality in your code;
You have to map out the way that particular vulnerability is impacting;
And then you have to work on rectifying the findings.
Such a process may only include four steps, however, it isn’t a trivial task.
One of the problems in overcoming the vulnerability challenge is that organisations, sometimes, have no clue that they are actually susceptible. The fact that the open source community has an extensive amount of data means that the vulnerabilities would be spread across that expansiveness. So, running automated scans for identifying vulnerabilities would never let them go unidentified.
Taking help of automation tools would not only help you get to the problem areas faster, but also keep doing it continuously. When you enforce automated tools to continually monitor security problems, you come closer to protecting your project and taking control over the open source components you are using.
Prioritising the involvement of the team in security
The last point to cover in order to overcome the open source challenges involves your team. There is a high likelihood that your developers would not be experts in security. And the people you may have in security would be lost in the developers’ realm. Since open source vulnerabilities require you to be efficient at both development and security, there has to be some training involved.
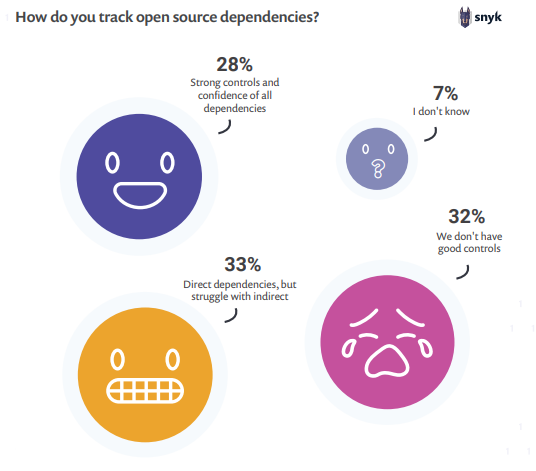
Such a response for detecting open source dependencies is not ideal. So, aim for cross training your staff, the developers should be able to at least identify certain security vulnerabilities and the security team should have some understanding of the development process.
If you think that isn’t a possibility, you can hire outside help to assist you in overcoming the challenges posed by the open source components.
The Verdict
OSS is on the rise and it will continue to grow in the future, there isn't any doubt about it. Along with that open source security will also strive to improve. Yes, there are issues that surround open source security, it isn’t perfect. I think that’s a good thing, because perfection cannot be improved upon and that means open source security has a lot of strides to make.
Open source security operates on visibility and openness, and it also teaches its adoptive organisations to preach the same. Aiming for visibility in your source code would always keep you ahead of the vulnerabilities you might have. It would also provide you with knowledge of your dependencies and a clear understanding of your code.
So, in that sense, open source software would be a great low cost addition to your project and open source security isn’t something that would ever hold you back. With the amount of open source security tools available today, that’s almost a guarantee.
Subscribe
Related Blogs
Trek n Tech Annual Retreat 2025: A 7-Day Workcation of OSL

OSL family came together for the Trek n Tech Annual Retreat 2025, a 7-day workcation set amidst the serene beauty of…
Exploring Drupal's Single Directory Components: A Game-Changer for Developers

Web development thrives on efficiency and organisation, and Drupal, our favourite CMS, is here to amp that up with its…
7 Quick Steps to Create API Documentation Using Postman
If you work with API , you are likely already familiar with Postman, the beloved REST Client trusted by countless…




