Technology has made our life super-fast and easy. Starting from shopping online to paying your bills, you can grab the world at your fingertips. But along with easy access through various applications, is technology providing you the necessary security? As security is considered a top priority that needs to be maintained due to the increase in cyber threats around the world. Unfortunately, vulnerability is seen in some of the organization's security ecosystem leading to the inability in building systematically secured software. Therefore, it is always advisable to build security in the initial stage so that no problems occur at the time of product deployment. There are various companies that do not have an approach of designing and building software based on core security principles required for the smooth functioning of applications. This article on secure software development lifecycle can be an eye-opener for all of us to emphasize the significance of building security into software development and make it the topmost priority.
The importance of security in software development
We all are aware of the fact that the information technology sector is one of the world’s fastest-growing industries. It is observed that the rate at which software and software products are progressing is many times greater in comparison to the rate at which software security is progressing. As a result, it gives rise to cyber threats and vulnerabilities. Many companies have witnessed such harmful attacks leading to damage to their brand reputation. For example, in 2011, Sony Pictures experienced a SQL injection attack by LulzSec (the hack-group), which released around 1 million user accounts, including passwords, email addresses, home addresses, birth dates, etc., which as a result violated the privacy policy of their service. HBO was attacked in the year 2017 when a hacker released a screenplay episode of a very popular TV series that wasn’t still broadcasted. The hacker also got access to financial documents, contact lists of actors and film crew, and other confidential information. In the same year of 2017, personally identifying data of hundreds of millions of people was stolen from Equifax, one of the credit reporting agencies that assess the financial health of nearly everyone in the United States.
So, all these well-known companies never expected such malicious attacks which led to heavy financial and reputational losses at their businesses. This is the reason why software security is so important for building up secured software advantageous for both its developers and users. There is a need for a secure path to production. Thus software security helps in strengthening the security posture and avoid any future cyber attacks.
How to enhance security in Software Development Life Cycle
It is seen that many companies have a software development life cycle (SDLC) process which produces software with the highest quality in a much disciplined and systematic way. Due to rising software security threats, it is essential to integrate security into all the stages of the software development life cycle (SDLC) to make it a secure SDLC. It is beneficial for organizations to adopt a secure software development life cycle (SSDLC) approach to reduce cyberattacks and threats. The good thing about SSDLC approach is that it is not only restricted to developers or the security team. But it can also be easily adopted by cross-functional teams to enable better security over several stages of the software development life cycle (SDLC). There is a need for Secure software development lifecycle policy that helps in providing safer software production. Having a Secure software development lifecycle policy template can help in improving security during various phases of software development. Let’s now get a better understanding of what exactly is a secure software development life cycle (SSDLC) and its various phases.
What is Secure Software Development Life Cycle (SSDLC)?
Secure Software Development Life Cycle (SSDLC) is a process of incorporating security into the Software Development Life Cycle (SDLC). It is basically, a framework defining the complete development process of a software product also building security in all the stages of SDLC i.e. starting from the planning to the design, development, testing, and deployment stage. There is a need to follow Secure software development lifecycle standards that can support the security of software production without any further concerns.
Here we will discuss the various types of Secure software development lifecycle phases. Take a look below.
5 Phases of Secure Software Development Life Cycle
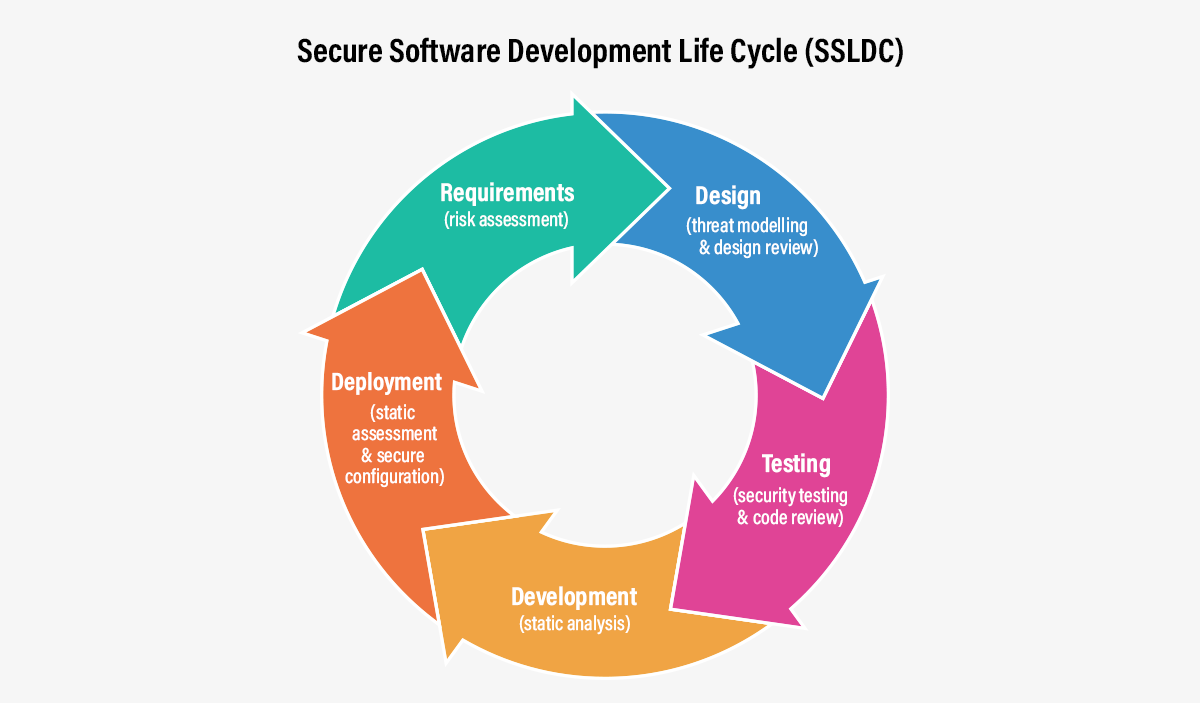
Phase 1: Requirement Collection and Analysis
During this phase, security requirements for the software application are established. The key security risks within the application such as functionality, type of information application being used, etc. are examined by the security experts. This phase helps in ensuring technical feasibility and providing quality assurance.
Phase 2: Design
This phase helps in building security into the design of the software application. The technical architects and lead developers create high-level design choices that meet the necessary functional and security requirements. It is observed that half of the software defects that create security problems are introduced in this stage. Therefore, the designs are reviewed in this phase to detect the software defects and solve them at the earliest.
Phase 3: Development
In this phase, it is ensured that code is developed securely so that no security threats and vulnerabilities occur. There are generally established secure coding guidelines and also code reviews that make sure that these guidelines have been followed correctly. The code reviews can be either manual or automated using technologies like static application security testing (SAST).
Phase 4: Testing
It is very important to test applications and software before they are made accessible to the users. Once the development process is done, the applications and software go through a rigorous testing cycle to meet the set security standards. Such a testing process helps to minimize the number of bugs witnessed by users. The tests include penetration testing, integration testing, further static code analysis, dynamic analysis, etc.
Phase 5: Deployment & Maintenance
In this phase, the application is made available to the user after finally checking all the security controls like secure code review (static analysis), dynamic, configuration, container security, etc. This is considered as the final stage after the applications and software go through the various phases of the Secure Software Development Life Cycle to improve the security aspect of software development.
The role of DevSecOps
Let me highlight here an important term DevSecOps which automates the integration of security at every phase of the software development lifecycle. It is necessary to understand the relationship between DevSecOps and SSDLC. Both the practices support each other in delivering the best services for enhancing security. They make sure that the developers are efficiently performing their tasks and going the extra mile to meet functional specifications apart from only spending time in writing and testing their code. DevSecOps represents a natural and essential evolution in the way companies approach security towards software development. It focuses on empowering the developers by giving them ownership of the production environment of applications from traditional IT teams. This further helps the developers to prioritize automating build, test, and release processes.
From the beginning of the development cycle, DevSecOps introduces security processes. The code is reviewed, audited, scanned, and tested for security issues throughout the development cycle. The issues are addressed at the earliest once they are identified. The DevSecOps practices also help in reducing time in resolving vulnerabilities and lessen the workload of the security team allowing them to prioritize other important tasks.
“The purpose and intent of DevSecOps is to build on the mindset that everyone is responsible for security with the goal of safely distributing security decisions at speed and scale to those who hold the highest level of context without sacrificing the safety required,” describes Shannon Lietz, co-author of the “DevSecOps Manifesto.” More on DecSecOps here.
What SDLC model is proposed by OWASP
One more way to provide security is through the OWASP Application Security Verification Standard (ASVS) Project. This facilitates a basis for testing web application technical security controls, further providing the developers the list, necessary for secure development. During the SDLC cycle, OWASP provides security in the following ways.
The Planning or requirement stage
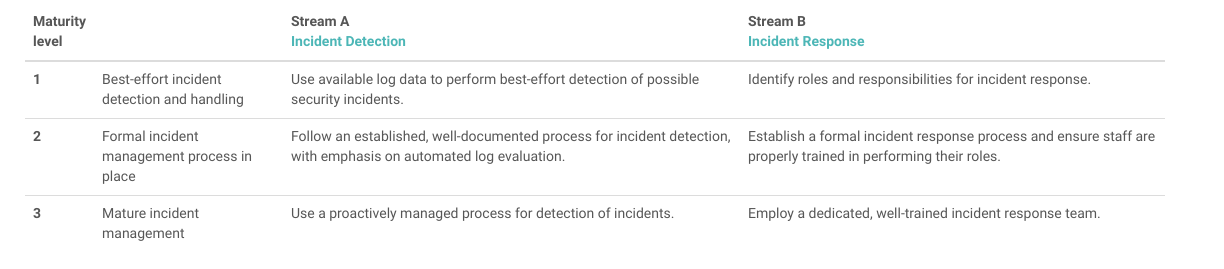
This particular process tries answering the following question, “What is the system going to do?” During this stage, the SAMM project provides 3 specific maturity levels including both in-house software development and third-party supplier security.
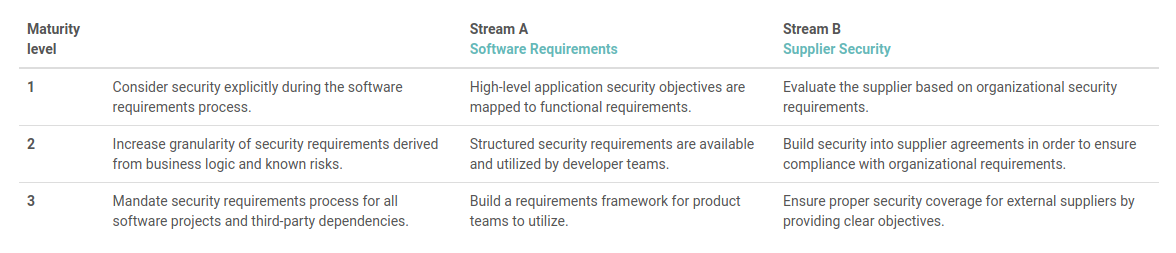
This is the best way to provide security at the start of the Software development process.
Design Stage
After the requirements are gathered then the execution specifics should be described. This stage depicts a diagram tracing data flows and common system architecture. The threat modelling can be practiced in this stage for better security. The concept of threat modelling will be discussed shortly, in the following paragraphs.
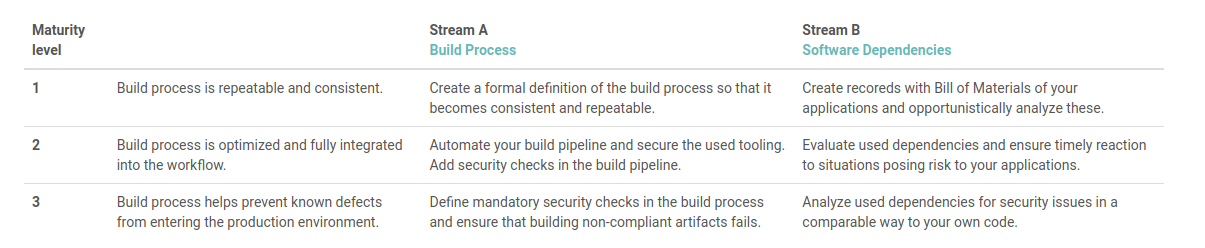
Development Stage
This step is very important as both the decisions and assumptions made in the previous stages will be examined. At this stage, the SAMM offers the following generic implementation considerations.
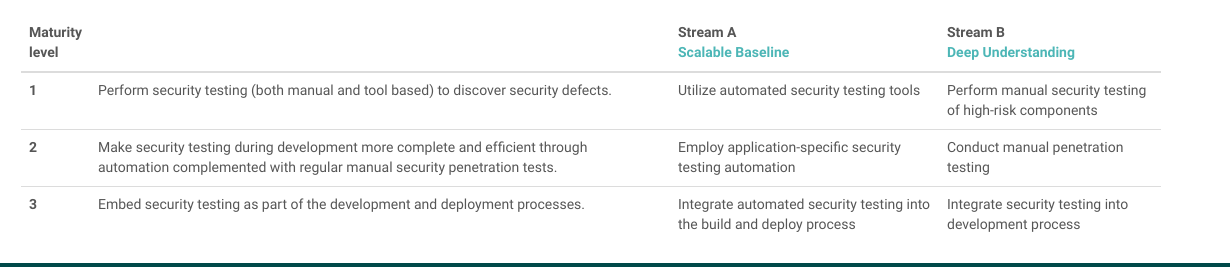
Testing Stage
This stage helps in validating software correctness and its an outcome for enhancing security-related decisions of all the other stages. Both manual and automated testing can be done in this stage. SAMM provides three maturity levels across Architecture Reviews, Requirements testing, and Security Testing.
Release Stage
This is the final stage of the software development life cycle. The ModSecurity Core Rule Set is used efficiently to detect and block several attacks. In this, SAMM offers a section on incident management, where simple questions are asked to the stakeholders to help one determine incident preparedness appropriately.
For better understanding, you can refer to a book named, “The Security Development Lifecycle: SDL: A Process for Developing Demonstrably More Secure Software (Developer Best Practices)” by Michael Howard and Steve Lipner.” This book mainly talks about the practical history of the SDL, and lessons to help you implement the SDL in any development organization.
Secure software development lifecycle best practices
Now, I would like to discuss a few practices which are adopted during the early stages of the Secure Software Development Life Cycle (SSDLC) to improve security. Take a look below:
Threat Modelling
Threat modeling is a process that is carried out in the development phase to safeguard the software application from cybersecurity threats and vulnerabilities. This technique helps in understanding how an attacker makes targets, locates entry points, and conducts attacks which further allows the development team to build up strategies to protect software and applications from any such potential threats and damages. It should be performed in the early stages of the software development life cycle as this enables the organizations to integrate security requirements into the design and implementation procedure. The adoption of this practice reduces the workload of developers as the potential issues are identified at an early stage allowing them to not struggle between meeting the software delivery deadlines and deploying a secure product to the users.
Architectural risk analysis
Architectural risk analysis is a technique that helps in identifying the threats and vulnerabilities during the design phase of the software development life cycle. This process includes the identification and evaluation of risks and risk impacts. It also helps in recommending risk-reducing measures. Architectural risk analysis studies threats and vulnerabilities that may be malicious or non-malicious in nature. With this process, the developers can analyze a software system from its component level to its environmental level to evaluate the threats and vulnerabilities at each level.
Attack trees
Attack trees provide a procedure to examine security controls, strengthen them, and respond to changes in security. Security can be considered as an ongoing process and attack trees are the basis of understanding the security process. Through a graphical representation that is easily understandable, the attack trees help to recognize the various ways in which an information system can be attacked and build countermeasures to prevent such attacks. Since this approach is used to design, implement and measure the attack, it can be considered as a practice conducted in the design phase of the SDLC.
Secure software development lifecycle training to developers
It is important for the developers to receive proper training on developing secure software and applications. The organizations can support the developers to build software applications while maintaining the security aspect with the following easy practices.
Providing practical experience. It will be beneficial to give practical examples which will encourage the developers to experience real-life scenarios rather than mere theoretical knowledge in terms of security training.
Availability of relevant courses. It will interest the developers to learn from examples and case studies matching the technology and platforms that they are currently using. This will make them learn things better and in a much more convenient way.
Guidance through online training. Through e-learning courses, the developers get to participate in security training according to their convenient time. It gives a good opportunity to learn complex material which can be reviewed by the developers whenever they want.
Incentives facility. The developers can be motivated by offering incentives after every course or series of courses.
Adopting open source is a great way of making sure security at all stages of software development. To know more, read the complete guide on open source security. To see an example, learn how you can incorporate secure SDLC in Drupal development.
Endnote
As we all know that security is an ever-evolving process. Therefore, a progressive organization cannot survive without getting serious about security, and the most convenient way to get serious is to integrate a secure software development life cycle into their work. Starting from requirements to design, coding to test, and finally till deployment of products the SSDLC tries to build security into a software product or an application at every step in the development process. Even though every organization will have its methodology to support software security, the approach should be effective in nature.
Subscribe
Related Blogs
UX Best Practices for Website Integrations

Website Integrations determine whether users stay engaged or abandon a site. I experienced this firsthand with a delivery…
How design thinking acts as a problem solving strategy?

The concept of design thinking is gaining popularity these days since people across different industries are using it as a…
10 major challenges that come across during an agile transformation

It’s no longer a mystery that agile was created as a response to the various concerns that the traditional waterfall…




