Do you remember Scrooge McDuck? He was the uncle to the most famous and beloved character - Donald Duck. Most notable for his piles of shiny, golden coins stacked in his cartoon mansion.
His favorite pastimes: Pinching pennies, counting gold and swimming around in his mountains of money.
While we can’t all have Scrooge McDuck’s limitless riches, we’re still like him in a few important ways. Among which guarding his riches in every sort of manner is one.

New technologies and approaches are creating massive changes that have forever altered the way consumers and businesses interact. Adding to these technological changes, our e-mail accounts and other social media handlings play a similar role as Scrooge McDuck’s riches. And having to log in to these treasures one by one is something we dodge to do.
Right?
Thus, here is one of the most trustworthy applications for your software systems.
Presenting Single Sign-On (SSO)
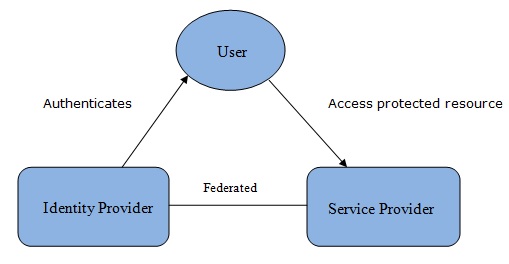
Single sign-on (SSO) is a session and user authentication service that allows a user to use a single set of login credentials (like a name and password) to enter multiple applications. In the SSO system, a third party service offers the identification and authorization mechanism and is responsible for informing the user identity.
This identification and authorization are handled with the help of Federated Identity.
Federated Identity refers to the standards, tools, and use-cases that enable the users to access multiple applications using the same access credentials.
So now the question is - how is the authorized data exchanged?
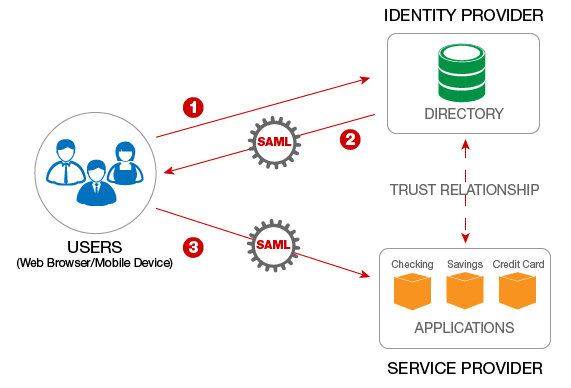
Well, Federated Identity comes with OASIS security assertion markup language (SAML) specification (It may involve open source technologies also). This specification helps in standard exchange of data between the security domain, having the main focus on providing support for:
SAML 2.0 as an Identity Provider: is the system or the domain that supports the user authentication and has associated attributes. In SAML, Identity Providers are also called SAML authorities and Asserting Parties
SAML 2.0 as a Service Provider: is the system or administrative domain that relies on information or the data supplied by the Identity Provider.
Security and Privacy in SAML 2.0
This protocol brings no security by itself and highly relies on secure communications (SSL and TLS) or some pre-existed trust relationship which also typically relies on PKI or asymmetric cryptography.
It represents a wide variety of security mechanisms to identify and guard the data against attacks. The relying party and asserting party should have a pre-existing trust relationship which typically depends on a Public Key Infrastructure (PKI).
When a party demands an assertion from another party, a bi-lateral authentication is needed. Among which SSL or TLS are the two that are recommended with the management of mutual authentication or authentication via digital signatures.
In terms of privacy, SAML 2.0 also promotes the establishment of pseudonyms between an identity provider and a service provider. The authentication context mechanisms enable a user to be authenticated at a sufficient and assured level ( appropriate to the resource that is attempting to access at the service provider)
SimpleSAMLphp for Implementing the standards of SAML 2.0
What is SimpleSAMLphp?
It is an application that is written in PHP which helps in implementing SAML 2.0. SimpleSAMLphp is a really easy way of integrating all the web-based PHP application into a federation.
SimpleSAMLphp maintains all the non-PHP scenarios by using the Auth Memcookie approach (a special cookie is added in Memcache that the Apache module Auth MemCookie understands).
It offers support to the two scenarios:
- SimpleSAMLphp as a Service Provider
- SimpleSAMLphp as an Identity Provider
Service Provider Scenario
It is important for the user to know that the Service Provider API presents with basic functionality.
- Verifying if the user is genuine or not
- Whether they need any authentication or not
- Login and Logout
- Preparing the user attributes
- Preparing the URLs for login and log out.
For authentication, SimpleSAMLphp connects to an identity provider (which is easily defined by configurated files). This is done so that the Service Provider easily configures to connect to other Identity Providers without having to modify anything in the web application.
In the web application, if the user wants to implement SimpleSAMLphp as a Service Provider, they need to add classes by using the API. Once the authentication is complete, they can easily access the user’s attributes.
Identity Provider Scenario
The identity provider in simpleSAMLphp is configured to validate the user against various origins - it may be static, LDAP, SQL, Radius, OpenID, Facebook, and Twitter.
For setting up the Identity Provider, configuration files are required to be changed so that the authentication module can be used and specified ( with additional information and the list of Service Providers). When several Services Providers utilize the same Identity Provider to verify the user, the user needs to log in only once. This is done because the session information is stored by the Identity Provider.
The Identity Provider also requires a certificate so that identification is proven to the Service Provider.
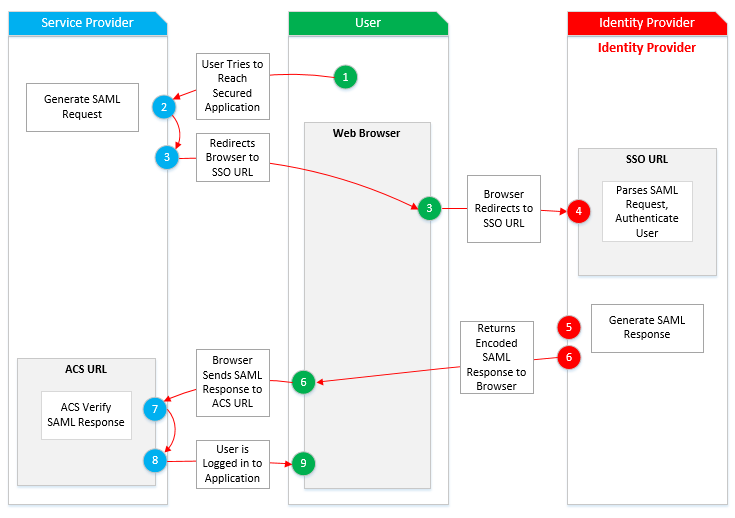
How are Sessions in SimpleSAMLphp?
SimpleSAMLphp consists of an abstraction layer for session management. That indicates it is possible to select between different kind of session stores, as well as write new session store plugins.
There are five ways in which the user can store their sessions in SAML. The five ways are:
PHP: If the user wants to use the PHP session handler, then they need to set the store.type configuration option in config.php. But they have to keep one thing in mind that the PHP does not allow two sessions to be open at the same time.
This indicates that if they are using PHP sessions, both the application as well as the SimpleSAMLphp at the same time, then they need to have different names.
SQL: To store session to a SQL database, set the store.type option to SQL. SimpleSAMLphp uses PDO (PHP objects) when entering the database server, so the database source is configured with the help of DSN (Data source name). The expected tables are generated automatically. If the user wants to store the data from multiple but a separate SimpleSAMLphp installation in the same database, then they can do the same by using the store.sql.prefix option to prevent conflicts.
Memcache: To store the Memcache session handler, the user needs to set the store.type parameter in config.php. memcache that enables them to store many redundant copies of sessions on various Memcache servers. Every server group is an array of the servers. The data or the information items are load-balanced between all types of servers in each and every server group.
Redis: To save sessions in Redis, the user need to set the store.type option to redis. By default, SimpleSAMLphp will strive to combine Redis on the localhost at the port 6379. It is, then, configured with the help of store.redis.host and store.redis.port options.
Writing your own plugin: In SimpleSAMLphp there is an excellent open source community, and every type of users are welcome to join. The forums are open for everyone to ask questions and queries, provide answers, inquire improvements or offer with code or plugins of their own.
Drupal in the picture
DrupalCamp 2018 talked about Drupal 8 module, simpleSAMLphp. The session was all about installing and configuring SimpleSAMLphp as IDP and SP. It also talked about integrating SimpleSAMLphp into Drupal 8 and create an SSO network.
Drupal SimpleSAMLphp module is one of the most robust and strong modules. It provides a comprehensive and complete implementation of SAML in PHP.
This module not only made it possible for Drupal to communicate with SAML or identity providers (IdP) to authenticate users but it also resulted in the Drupal site to act effectively as a SAML or Shibboleth service provider (SP). Some of the features provided by it are:
- The module provides with in-time provisioning to the accounts of the Drupal user which are based on SAML attributes.
- It provides with automatic role assignment that is based on SAML attributes
- The dual mode in the module guides the users with traditional Drupal accounts and SAML-authenticated accounts at the same time.
- It supports multiple authentication protocols like OpenID (e.g., Google, Yahoo), Facebook, OAuth (e.g., Twitter), Radius etc
Conclusion
SimpleSAMLphp is very valuable and important for executing an SSO mechanism in web applications. It is developed in a native PHP and maintains integration to any SAML providers.
Yes, the library is very flexible and it comes with many authentication modules and furthermore, they can easily be adapted to third-party applications.
The technology has become very popular especially with the rise of concepts like Web 2.0 and the continuous development of social networks websites like Facebook, MySpace, and others.
At OpenSense Labs, we believe that security is the number one concern of any organization and we try to provide them with services that help them in a longer run. Ping us now at [email protected], our professionals would provide you with suitable answers to all your queries and questions.
Subscribe
Related Blogs
Exploring Drupal's Single Directory Components: A Game-Changer for Developers

Web development thrives on efficiency and organisation, and Drupal, our favourite CMS, is here to amp that up with its…
7 Quick Steps to Create API Documentation Using Postman
If you work with API , you are likely already familiar with Postman, the beloved REST Client trusted by countless…
What is Product Engineering Life Cycle?

Imagine constructing a house without a blueprint or a set of plans. It will be challenging to estimate the cost and labor…