Keeping the security and privacy of the data always on the check is said to be one of the key exercises for organizations of all shapes and sizes. Small, medium or large scale when it comes to digital threats or things harnessing the privacy and security of the data and information a semantic approach needs to be followed for the same. Ransomware, legal battles, DDoS (Distributed Denial of Service) are the few digital threats bringing additional responsibility for an organization.

How come an organization will prioritize or manage the schedules in case of such emergent situations? The answer lies deep down in history which popped a new term called Design Thinking.
Let us move ahead and find out how with the help of an effective design thinking capability, the issues related to data threats and privacy can be handled.
What is Design Thinking?
Design Thinking encloses both theory and a process, completely focused on offering solutions for the complex problems in a highly customer-centric approach. Having a designer’s mindset will revolutionize the way organizations used to develop products, services, and strategies by bringing innovation with the human point, technologically and economic feasibility on one plate. It enhances the horizons for the people who are not even related to the designing at all as they turn up using the creative tools to act on a wide range of challenges.
Tim Brown, CEO of IDEO, refers to Design Thinking as, “A human-centered approach to innovation that draws from the designer's toolkit to integrate the needs of people, the possibilities of technology, and the requirements for business success.”
The essence of design thinking is very much simplified, it is a proactive approach striving to meet customer needs digitally with iterations and prototypes building empathy for the users. Along with this, it has been seen as a set of procedures to maximize business latitudes. When readdressing design thinking in the context of data or information, it can be described as a method to generate innovative solutions by addressing the data challenges, based on a customer-centric collaborative approach.
Roger Martin’s Knowledge Funnel, in his popular work The Design of Business, segments it into three divisions enabling businesses to innovate persistently. It consists of three phases, Mystery, Heuristics, and Algorithm.
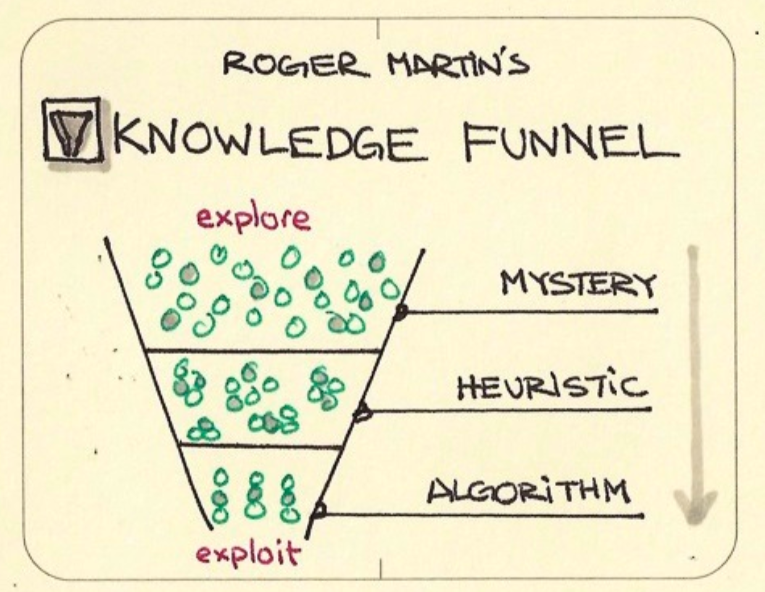
The mystery is all about the exploration, that is, queries, problems, symptoms, etc. Heuristic involves a deeper analysis and transitions of the issues or a bunch of problems from multiple perspectives. In the algorithm stage, a fixed and repeatable transition for the final solution is made.

Approaching the Challenges of the Current Data Strategy
Savy Sriram, Global Head, Retail Risk Data Strategy & Oversight at Citigroup, recommended a new insight on the concept of Design Thinking at CDO Summit in 2016. She stated when Steve Jobs considered design thinking as a precursor for the creation of the iPhone and iPad, we can also proceed in the same order to address the data-related challenges.
She further adds data is created long before it reaches a user or a member’s eye and by the time the organizations decide to use it, the technology advancements make it outdated. Technology empowers business models with the help of which organizations are able to build products, offer services. In the process, sometimes it has been presumed that customer engagement is made, but all in vain. Till the time, synchronization of customers and technology happens, customers are advanced to the more updated technology, a drawback for the organization.
These projects, no matter which vertical, organizations have to deal with dual situations when it comes to the associated challenges. With the limited time frame, restricted budget, and resources, organizations have to meet both the progressing regulations and compliance standards on data quality, collection, retention, usage, privacy, security, etc and further using data to drive revenue.
Applying best practices in digital security and privacy with design thinking
Empathize

Design thinking is all about connecting with the human element of anything. Commence by walking on the user's shoes, that is, considering and understanding the nature, emotion, and driving force for customers and employees along with their technological needs. Later, with design thinking work towards the deployment of the solutions in the distinctive real-world work context. The employed solutions have not always got to be placed in the best-case environment where the implementation of a complex situation is very much feasible.
In order to have an idea about the data capture, access, and communication path, it is imperative to recognize the valuable assets, their current and previous accessibility details. In addition to that, how the data, tools, and practices are being used by the employees or the users to get a comprehension of the type of data held, the place where it has been kept and through which channel it is communicated inward and outward of the organization.
The aforementioned information is needed by the organization’s figureheads to bid the privacy and security of the data as there are players out there that can steal or exploit an organization's information assets.
Moreover, design thinking fits very well in the case of the information security domain. With design thinking, cybersecurity controls can be easily coupled into a user’s environment and attention to any complications or any personal considerations that might entangle any cohesion that can be addressed and also accurate solutions for all the related concerns are offered with design thinking.
Map

Keeping an inventory of everything that is digitally available, intangible and hardware. This list proves to be beneficial in finding the entry points for the attacker, mapping who has access at what levels, he can use to breach to get the data or information access.
Prioritize

Once the interpretation of the organization's assets has been done, the next step is to calculate the process to address them efficiently. Follow an analytical approach to deploy the solutions for all the appearing issues or problems. At the very first, technical problems are defined and then is forked to formulate the technical solutions for the same. This is vital and substantial to achieve information security.
Design thinking enhances the thought process beyond the fold. Organizations are working head to toes to develop and deploy new products and security measures with the analytical design thinking approach meeting the long term data security and privacy objectives. With design thinking thoughtfully integrated solutions are built where every other product works in congruence with others.
Iterate

Design thinking focuses on working block by block on a cropped issue or problem. A long term solution plan will do no harm and also will bring no major benefits for the organization. Design thinking lets a user think long term but focus on taking baby steps to reach the ultimate goal.
To begin with the building of small prototypes, refining, and removal of elements on the basis of what is working or what is not. Holding up to the experimentation to prove or disprove ideas and constant adjustment to the user’s feedback.
The aforementioned gels very well with information security too. Risk management follows the road of a rigid iterative cycle, PDCA (Plan, Do, Check, Act). With design thinking it gets replaced to a more flexible model, ITPR (Iterate, Prototype, Test and Refine), offering solutions to real-world problems by connecting with the human element of the same.
Conclusion
As the world becoming closer through the Internet, the security of data and pieces of information getting exchanged has become imperative to keep guard of. Handling data and information with care by keeping transparent practices will help to maximize the trust of the customers.
Defining in simplest words, design thinking is a way in which designers think about building an effective solution for any idea or a problem. It takes the path of a set of cognitive processes to resolve an issue. The methods in design thinking will take a human-centric approach for security, aiding human adherence and bringing fruitful solutions for the same.
Subscribe
Related Blogs
How design thinking acts as a problem solving strategy?

The concept of design thinking is gaining popularity these days since people across different industries are using it as a…
10 major challenges that come across during an agile transformation

It’s no longer a mystery that agile was created as a response to the various concerns that the traditional waterfall…
Design as a team: An extensive guide to cross-functional collaboration

Cross-functional collaboration plays a vital role in accelerating the delivery of better results for consumers. It promotes…



